Smart Monitoring Era
Senslink 3.0
The AnaSystem Cloud IoT Platform automatically transmits monitoring data to the Senslink cloud data collection platform through the intelligent messaging recorder SensMini A4. This shifts the data center that customers previously had to build themselves to a telecom operator's data center, providing a public cloud service where all issues related to equipment, power, network, and cybersecurity are managed by professionals. As long as there is an internet connection, monitoring data can be queried immediately through the web.
Senslink also offers data sharing and standard data exchange (Web Service) for integration with other software. Additionally, it provides a license for the Senslink private cloud platform, allowing the data platform to be set up on internal servers for dedicated private cloud services.
Distributed architecture storage
API painless technology transfer
Integrated Monitoring Platform
Provide real-time computing modules
Cloud maintenance and cybersecurity protection
IoT makes it easy to connect devices to the cloud
Features

AI Analysis
Automatic Update Status
Multi-Select Monitoring Station Theme Display
Custom / View Jurisdiction Monitoring Station
Distributed Architecture
The platform can be expanded according to needs
Easy maintenance
Reduces the risk of total system downtime

Open data
Complete API documentation
Third-party entities can access data through the API interface
No fees are required for API calls and data reception

Line / Email Notification
Automatic update status
Multi-select monitoring station theme display
Custom / View jurisdiction monitoring station
Computing module
Abnormal data comparison & alert judgment
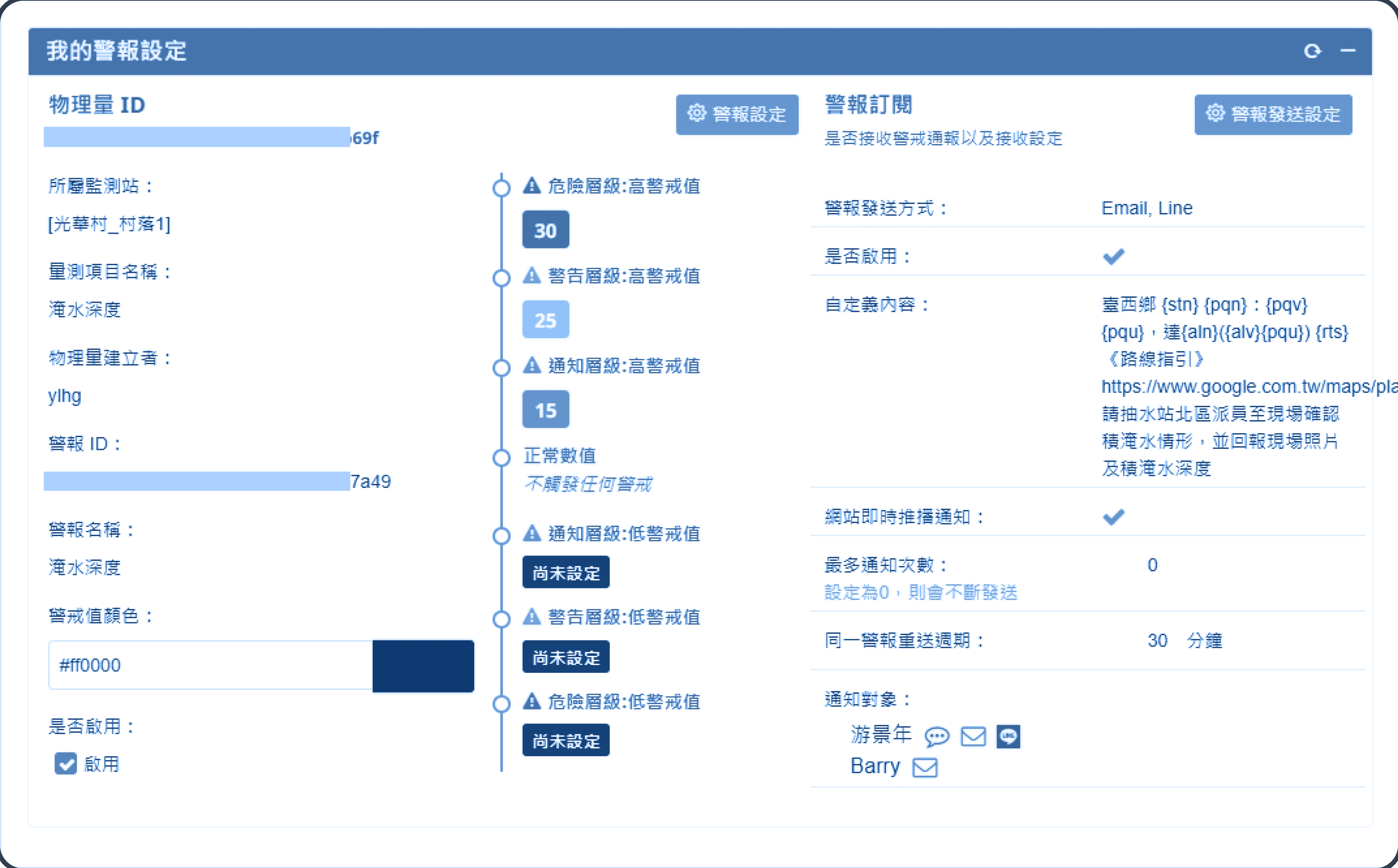
Users can set warning values for each physical quantity, and the system continuously monitors the physical quantities and records those that exceed the warning values.
Users can set their own requirements for receiving alert notifications.
Abnormal value filtering
Algorithms can automatically filter out data anomalies caused by unreasonable factors, making the data more accurate.
Cross-test item operation - multiple variable cross-physical quantity operations
Users can freely combine multiple physical quantities for arithmetic operations according to their own needs without restrictions.
Distributed Architecture
Save
Distributed architecture that can be continuously expanded as needed.
Hybrid database (TSDB, MySQL, Redis) service
ElasticSearch Data Analysis
MQTT
Abnormal value filtering
Algorithms can automatically filter out data anomalies caused by unreasonable factors, making the data more accurate.
Internet of Things IoT architecture
Connect devices online through the interface
User-friendly interface, easy device activation
Replace devices anytime, 24 hours a day
Activate devices without regional restrictions
IoT devices upload directly to the cloud platform
Devices with IoT characteristics can upload data to the cloud platform anytime and anywhere as long as they have internet access, without limitations
Connects thousands of IoT devices
No limit on the number of devices

Cloud cybersecurity protection
Identity management
You can freely manage the client secret and client id.
Users can easily turn the end-user login key on and off using a friendly interface.
Backup mechanism
When the hardware and software resources are sufficient, enabling the redundancy mechanism can achieve high availability.
The same web service, such as a website, can be hosted on different server machines, and if one of them fails, the web service will not be affected.
Data Backup
Data backup is the last line of defense for system operations. When a major incident causes data damage, it can be quickly restored from regular backups.
Cybersecurity protection
When designing and developing hardware and software, there may be oversights that lead to system vulnerabilities. Use vulnerability scanning tools to check for known cybersecurity vulnerabilities and apply corresponding patches to avoid being exploited by hackers.
Cybersecurity incident response
When a cybersecurity incident occurs, the response measures taken include switching to backup systems, restoring from backup data, temporarily shutting down external services, and assessing the extent of the damage. This involves reporting to relevant parties, investigating the error through system logs, and carrying out recovery operations.
Integrated Monitoring Platform
Real-time monitoring
Present monitoring data based on the station for users to keep track of the status of monitored physical quantities at any time. The data update cycle depends on the device feedback cycle.
The monitoring station can be customized to group based on user needs, not limited to displaying a single measurement station, providing various combination options.
Dashboard
A single-page overview of real-time data for specific stations in table format. Users can group the stations according to their needs, and each group (drop-down menu) can be displayed independently, creating a customized information dashboard.
Historical data
According to user needs, retrieve statistics (non-real-time) data for specified monitoring stations within a specific period. Offers a variety of time intervals and data calculation methods (average, maximum, sum, etc.) for selection. Customizable settings make it easier for users to apply the data for convenient querying.
automated robot
Multivariable operations, that is, the calculation of different physical quantities, are applicable when local equipment is insufficient. It uses the relationship of equipment installation positions to calculate the information the user wishes to view.
Push Notification Settings
Monitoring physical quantities can set 6 levels of alert notifications, allowing customization of sending frequency and notification messages. It uses current mail and social media (such as line) to send immediate information, featuring a highly flexible configuration for automated alert notification.
Data community sharing
With the concept of shared creation, data owners can share data (physical quantities) with community members, and can set sharing permissions for different monitoring items, reducing the data transmission process and significantly increasing the benefits of public application of data.